App-V Hidden Drive Letter ADM File
In our environment, our users love their drive letters, and they do so to the Nth degree. As part of a change control process, myself and a colleague have scheduled the deployment of the App-V Client across our business estate to allow us to begin provding the users with user-centric real-time streamed applications to meet their business needs.
We today discovered the true nature of our Nth degree network drive letter because after some review, it became aparent that not a single letter (beyond the usual C, D, E for local disks) was free for company-wide use which caused us pain on the inside. We came to the conslucsion that people in our business very rarely use floppy disk drives anymore, and even less people (zero to my best guess) use a second floppy disk drive, which means that the B: drive would be available across the estate.
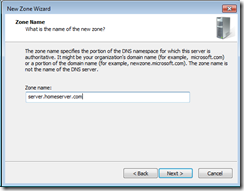
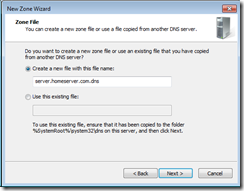
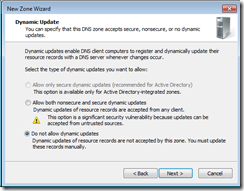
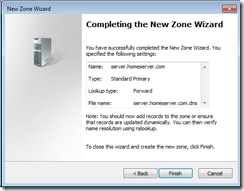
Using the Microsoft App-V ADM file for Group Policy (available for download from http://www.microsoft.com/download/en/details.aspx?displaylang=en&id=25070), I re-configured our GPO to force the clients to use the B: drive instead of the App-V default Q: drive. I tested the configuration change on my own machine (ICT dogfooding for everyone), and also streamed a couple of applications to verify the drive letter change didn’t cause any issues, and I came to an idea. If the App-V virtual file system is inaccessible by the user because of the ACLs that App-V applies to it, and because the user has no reason to be meddling in the App-V virtual file system drive, why, display it to them?
I took a look at the Windows Explorer, Hide these specified drives in My Computer policy in the User Configuration portion of Group Policy however for reasons beyond me, Microsoft only gave you a very limited set of options in this policy (Hide A, Hide A and B, Hide A, B and C, or Hide All Drives). This policy was probably useful in the legacy days where you only wanted to restrict use of local floppy disk drives, however it’s not very useful in the 21st century.
The way around this, is to build your own custom ADM file to change the options for disabling the drive letters.
I have this evening created a custom ADM file for such a purpose, and in my example, the file is crafted to allow you to hide the B drive, or no drives, however you can add as many options to this file as you like.
How you configure the file to restrict particular drives is based on a binary value using a reverse alphabet table. Details for calculating this can be found on the Microsoft Support article Using Group Policy to Hide Specific Drives (http://support.microsoft.com/kb/231289). If you aren’t ocomfortable trying to do this in your head, you can simply copy and paste the table out of the article into Notepad and do your working in there.
Simply add the ADM file to an existing GPO and link it to an OU which contains users in AD, and you’re all set.
If you want to only restrict a single letter, then you can simply edit my file by modifying the label for, and the binary value for the BOnly item. The file is shared and free for you to download from my Windows Live SkyDrive account. I’m also happy to take comments or answer emails with questions about how to modify the file.