Over the course of the last few days, there has been much said online about a security flaw which is affecting the X86 CPU architecture and more specifically Intel CPUs*. This is an issue which has been known since earlier in 2017 but has only recently started doing the rounds. The issue was uncovered by […]
Over the course of the last few days, there has been much said online about a security flaw which is affecting the X86 CPU architecture and more specifically Intel CPUs*. This is an issue which has been known since earlier in 2017 but has only recently started doing the rounds. The issue was uncovered by Google (https://security.googleblog.com/2018/01/todays-cpu-vulnerability-what-you-need.html?m=1) and was not scheduled to be made public just yet, however, growing information and leaks online led Google to release it early. The issue has also been logged under three CVEs: CVE-2017-5715, CVE-2017-5753, and CVE-2017-5754. Microsoft also has their own article at https://support.microsoft.com/en-us/help/4073119/windows-client-guidance-for-it-pros-to-protect-against-speculative-exe.
The early release by Google prompted various things that were already in-play to also happen early. Microsoft was forced to release the hotfix for Windows immediately and the Microsoft Azure planned VM maintenance which was scheduled for the 10th January has been brought forward to happen almost immediately.
* There are numerous reports including the original publication from Google that the issues also affect ARM and AMD CPUs as well. I do not wish to get embroiled in a debate whether or not AMD and ARM are affected as there is arguments coming from both sides. For the purposes of this article, I will focus on Intel as we know 100% that their processors are affected. Intel is keen to point out that while they are still affected, CPUs based on the newer platforms like Skylake and Kaby Lake will experience a lesser performance drop-off.
The Issue
So what actually is the fuss? The fuss is because of something called Speculative Execution. This feature of a processor is designed to improve performance by guessing what the processor is likely to be needed for next and trying to prefetch some of that data. A flaw in this process allows an unauthorised individual to read kernel level memory from the processor. What that means in English is that even a lowly browser-based JavaScript can read this privileged information; just by browsing a website with the wrong JavaScript file loaded could dump all the data out of your processor.
On a single machine, this is bad enough with the potential for a password, a Kerberos Ticket, some SSH Keys, a certificate private key, and more being leaked but it gets really bad in a shared environment. In an environment where VMware ESXi, Hyper-V, or another hypervisor is in use, this could return data from the CPU about other virtual machines on the host. In a cloud environment like Amazon AWS EC2 instances or Microsoft Azure IaaS VMs, this could allow data to be read back from a VM belonging to another tenant running on the same host.
The Fix
The fix for the issue is the complicated part. This is not something Intel is able to fix, or at least that’s what we believe currently, using new drivers or microcode against the CPU. The fix is having to come from the OS vendors like Linux and Microsoft Windows and the thing that has most people in arms is the impact. The fix itself involves the vendors having to rewrite a portion of the OS kernel, the very core of the operating system to work around the issue. Reports so far are showing that performance of certain I/O operations will be impacted by between 5 and 30 percent once the patch is applied with database and file servers most likely to take the hit. One very bad example I was shown depicts a PostgreSQL database and a SELECT query increasing from 3.8 seconds before the kernel update to 15 seconds after the update – that is a 500 percent increase!
Results are going to vary from system to system dependant on workload but in any case, the prognosis is not good. If you have a system that is tightly specified to run a specific task and a specific performance level it is possible it could all go out the window. I suspect we will be seeing and reading about impact and effects of this for months to come.
Patching Windows
The main purpose of this article is to cover patching Windows. The Microsoft hotfix for the issue has been released for Windows 7 SP1 and all later operating systems including client and server variants. Before I go ahead and provide the links to the download, there are a few things to note:
- Microsoft has released a PowerShell Module which you can install via the Install-Module command to discover a machines vulnerability and patch status (more on that in a minute)
- Installing the hotfix requires that your anti-virus software is compliant with the Kernel changes
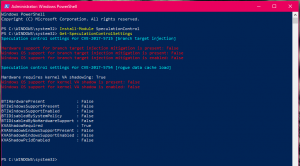
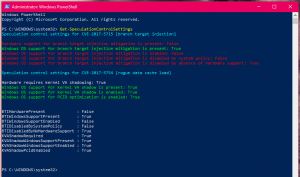
For the PowerShell Module, you can install it and run it without leaving PowerShell or a restart. As you will see in the image below, after running the script before a restart, everything is red which means I am vulnerable.
After applying the hotfix to Windows, things start to turn green to show that they are protected against. What is really key to note there though is that the first CVE, CVE-2017-5715 is not fully protected until both the Windows patch and a vendor provided firmware update is applied. In the screenshot below you can see that I have the Windows update installed but at the time of writing, Dell has not yet released an update for my Latitude E7450 laptop. Microsoft has already committed to releasing a Surface family update via Windows Update as soon as possible.
The second part, the anti-virus compatibility requires the software makers to acknowledge that they have updated their software to understand the Kernel changes made to Windows. This is being managed by a registry key and a user online has posted a Google Doc Spreadsheet listing the vendors, the products and the support at https://docs.google.com/spreadsheets/d/184wcDt9I9TUNFFbsAVLpzAtckQxYiuirADzf3cL42FQ/edit#gid=0. At the time of writing only Windows Defender (SCEP), Kaspersky, and ESET have added support in their latest update.
Once you have confirmed your threat status and whether your AV is supported, you can either get the updates through Windows Update or manually from the Microsoft Update Catalog. You will not be offered the update via Windows Update unless your AV is up to date and supported.
Windows 10 1709 and Windows Server 2016 1709 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056892%20
Windows 10 1607 and Windows Server 2016 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056890%20
Windows 8.1 and Windows Server 2012 R2 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056898
Windows 7 SP1 and Server 2008 R2 SP1 https://www.catalog.update.microsoft.com/Search.aspx?q=KB4056897
Update 1: Intel has a page listing manufacturer links for the hardware updates. For my device, the Latitude E7450 it is scheduled for release on the 10th January 2018. Visit https://www.intel.com/content/www/us/en/support/articles/000025619/software.html for a list of vendors and links to their own support information.
Update 2: Microsoft has now released application-specific guidance for SQL Server, Hyper-V, Remote Desktop Services, and Container Hosts. An article which lists available SQL Server updates to address SQL specific concerns is at https://support.microsoft.com/en-us/help/4073225/guidance-for-sql-server. The article with additional steps required to be taken on Hyper-V, RD Session Host, and Container Hosts can be found at https://support.microsoft.com/en-gb/help/4072698/windows-server-guidance-to-protect-against-the-speculative-execution.