In this post I’m going to assume that you’ve already installed UR4 in your Configuration Manager environment as that’s covered by many a post and article online already. I’m also going to assume that your UR4 Software Packages have been distributed to your Distribution Points.
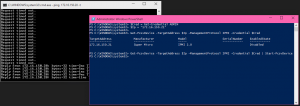
After you’ve installed Update Rollup 4 for Configuration Manager on your Primary Site Server and updated your site database, it’s time to update the rest of the servers in your Configuration Manager hierarchy and then move on to your agents and administration consoles. The first thing to do is we want to create some device collections to help us. I have created the following collections using the included WQL statements for the query based membership.
Creating the Query Based Collections
Configuration Manager 2012 R2 Agent (x64)
SELECT
SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System INNER JOIN SMS_G_SYSTEM_COMPUTER_SYSTEM on SMS_G_System_COMPUTER_SYSTEM.ResourceId = SMS_R_System.ResourceId WHERE SMS_R_System.ClientVersion = "5.00.7958.1000" AND SMS_G_System_COMPUTER_SYSTEM.SystemType = "x64-based PC"
Configuration Manager 2012 R2 Agent (x86)
SELECT
SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System INNER JOIN SMS_G_SYSTEM_COMPUTER_SYSTEM on SMS_G_System_COMPUTER_SYSTEM.ResourceId = SMS_R_System.ResourceId WHERE SMS_R_System.ClientVersion = "5.00.7958.1000" AND SMS_G_System_COMPUTER_SYSTEM.SystemType = "x86-based PC"
Configuration Manager 2012 R2 Console
SELECT
SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client FROM SMS_R_System INNER JOIN SMS_G_System_ADD_REMOVE_PROGRAMS on SMS_G_System_ADD_REMOVE_PROGRAMS.ResourceID = SMS_R_System.ResourceId WHERE SMS_G_System_ADD_REMOVE_PROGRAMS.DisplayName = "System Center 2012 R2 Configuration Manager Console" AND SMS_G_System_ADD_REMOVE_PROGRAMS.Version = "5.00.7958.1000"
Configuration Manager 2012 R2 UR4 Agent (x64)
SELECT
SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System INNER JOIN SMS_G_SYSTEM_COMPUTER_SYSTEM on SMS_G_System_COMPUTER_SYSTEM.ResourceId = SMS_R_System.ResourceId WHERE SMS_R_System.ClientVersion = "5.00.7958.1501" AND SMS_G_System_COMPUTER_SYSTEM.SystemType = "x64-based PC"
Configuration Manager 2012 R2 UR4 Agent (x86)
SELECT
SMS_R_SYSTEM.ResourceID,SMS_R_SYSTEM.ResourceType,SMS_R_SYSTEM.Name,SMS_R_SYSTEM.SMSUniqueIdentifier,SMS_R_SYSTEM.ResourceDomainORWorkgroup,SMS_R_SYSTEM.Client from SMS_R_System INNER JOIN SMS_G_SYSTEM_COMPUTER_SYSTEM on SMS_G_System_COMPUTER_SYSTEM.ResourceId = SMS_R_System.ResourceId WHERE SMS_R_System.ClientVersion = "5.00.7958.1501" AND SMS_G_System_COMPUTER_SYSTEM.SystemType = "x86-based PC"
Deploying the Software Packages for Agents
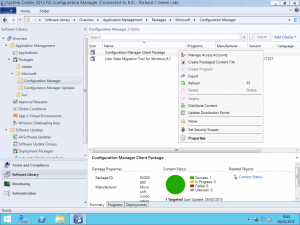
With the collections now created, head over to the Software Library node of the console. As part of installing UR4, the installer will have automatically created four software packages for you, two for the client architectures, one for the console and one for servers.
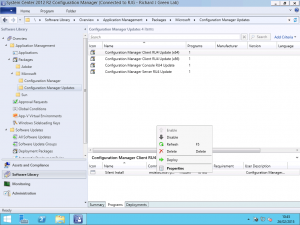
Clicking one of the Software Packages in the upper half of the view reveals the details of the package in the lower half. Select the Programs tab in the lower half and you will see the Program associated with the Software Package. Right-click the Program and select the Deploy option from the context menu as shown below.
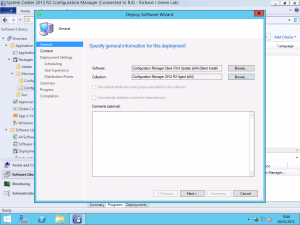
After clicking this, the Deploy Software Wizard will be shown. The Software field will be automatically populated by the wizard; we just need to enter the collection to target the deployment. For example, we want to deploy the UR4 update to all clients which have the out-of-the-box version installed so we need to target the Configuration Manager Client RU4 Update (x64) software program to the Configuration Manager 2012 R2 Agent (x64) collection.
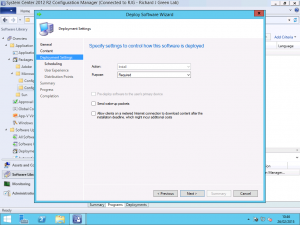
On the next tab, we need to change the default Purpose from Available to Required. This purpose will force the installation to occur according to a schedule which we set on the following panel.
On the scheduling panel next up, we want to configure the schedule in accordance with any change control we may have to comply with. In my lab environment, I simply want to push all of the agent updates out to the servers and clients as soon as possible so the As Soon as Possible option is ideal for me.
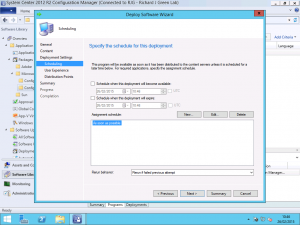
If you aren’t using Maintenance Windows on any of your collections in Configuration Manager you can click next through to finish on the wizard now and have your agent deployment begin. If you are using Maintenance Windows then you will want to pay attention to a setting on the following panel.
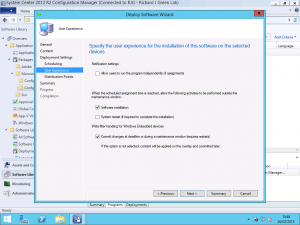
If you are using Maintenance Windows then you may want to select the Software Installation checkbox to allow the agent installation to occur outside of any windows. The agent installation does not require a restart and in most cases, should be updated in a couple of minutes with no fuss so there is really isn’t a reason to not allow this to happen. Ticking the Software Installation checkbox allows the agent upgrade to take place outside of any maintenance windows so it will take place as soon as possible.
Once you have completed the wizard, you can confirm that your Deployment was successfully stored by viewing the Deployments tab in the lower half of the Software Library Packages view. As shown below, you can see that the deployment I just created to deploy the 64-bit agent has been stored. With this completed, you will want to repeat the process for the x86 (32-bit) agent so that both types of client get the UR4 agent update.
Deploying the Software Package for Admin Consoles
I’m not going to walk through the process for this as it is the same as above for the agent update however there is one important difference I will cover.
When you get to the Deployment Settings panel, you need to select the Available deployment option and not the Required option. The reason for this is that when you deploy the UR4 agent updates, the agent version gets updated from 5.00.7958.1000 to 5.00.7958.1501 however installing UR4 for the Admin Console does not update the version number reported for the console in Programs and Features in Control Panel.
With the Admin Console, because the version number does not change, if the deployment was set to Required, clients would install the update package and would continue to re-evaluate it because it would still be detected as the old version not the UR4 version. What we need to do instead is advertise it to computers with the Admin Console installed and make it available for those users to initiate themselves.
If anyone knows of a different way to target the Admin Console UR4 update, perhaps using the installed Software Update detection I would really like to hear how you have been able to have it automatically installed as Required as that would save a tonne of headache and effort. In the meantime, enjoy your UR4 client rollout. In another post, I will be covering how to update your base client package with UR4 so that newly deployed clients get this updated version hassle free.