Yammer Enterprise for Office 365
If you have an Office 365 subscription on any plan Small Business Essentials or above, you will be entitled to Yammer Enterprise. Yammer, if you are unaware is an enterprise social networking product that Microsoft acquired a while back and is billed to replace the social features in SharePoint Online over time. Enterprise social networking I think is like marmite and some companies promote the idea whilst others shy away from it which I think has held back adoption and therefore, Yammer isn’t as widely used as you would think, especially for a free service as part of your existing Office 365 license.
Regardless of this, in this post, I will walk you through the very simply steps to activate your Yammer Enterprise network for your Office 365 Tenant and explain some of the next steps you can take to make Yammer more integrated into your business functions and make it more functional for end-users.
Activate Your Yammer Enterprise Network
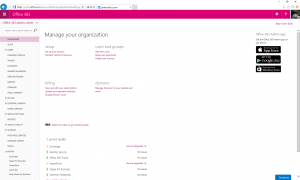
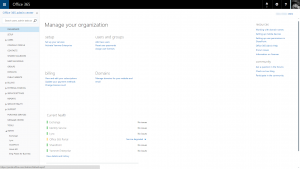
Activating the Yammer Enterprise Network is actually very simple. First, login to your Office 365 Admin Center as a Global Admin.
From the Dashboard presented when you login, you will have an option for Activate Yammer Enterprise under the Manage Your Organisation heading. Once you have selected this, you will be taken to the domain selection page.
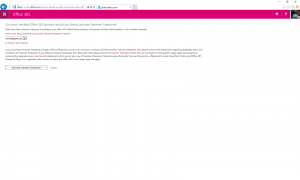
On this page, you must select which of your verified Office 365 domains you want to activate Yammer for.
Yammer is designed primarily for single domain use so if you work at an organisation which has multiple domain names such as regional domains for each country or territory that you operate in then you will need to activate your Yammer Enterprise network for one domain initially. Once you have your network setup with a single domain, you can follow the instructions on the TechNet article Combine Multiple Yammer Networks (https://technet.microsoft.com/en-us/library/dn804812(v=office.15).aspx) to contact Yammer Technical Support to add the secondary domains.
Once you have selected your domain and you select the Activate Yammer Enterprise button, after a few minutes your new Yammer network will be created.
By design, Office 365 Global Admins will automatically be provisioned as Network Admins in Yammer to administer your network however I found this didn’t work as it should and I had to follow a fix I found on the Office 365 Community by adding a new Global Admin afer the network creation which did get added to Yammer and then I logged in as that user and re-added my other Global Admins manually.
Syncing Domain Users to Yammer with DSync
Whilst Yammer Enterprise is made available via your Office 365 Tenant and allows your users to use their Office 365 credentials for logging in to Yammer Enterprise (be it as a cloud user, an on-premise AD user via DirSync or AADSync or whether you have ADFS setup and configured), the user on-boarding and off-boarding processes for Yammer are distinct. What this means for your end-users is that whilst they can visit yammer.com and try and login using their Office 365 credentials, they actually need to be registered in your network first.
Microsoft provides a tool called Yammer Directory Sync or DSync which functions in a similar fashion to the DirSync or AADSync tools for Azure Active Directory. The DSync tool doesn’t sync any passwords because those are provided via Office 365 and Azure Active Directory however DSync will sync the Name, Job Title, Office, Telephone and Mobile fields of an AD object to Yammer and will provision an account for the user. Setting up Yammer DSync is outside of the scope of this post but you can find out more from the TechNet article Install Yammer Directory Sync (https://technet.microsoft.com/en-gb/library/dn799032).
Yammer Directory Sync will automatically create Yammer users in your network as new AD users are created and it will also remove users when they are deleted from AD covering off the provision and deprovision processes. As you would expect, the tool updates user attributes as they are changed in AD.
If you don’t setup Yammer Directory Sync then each of your users will need to manually register for Yammer the first time they visit the site and accounts will not be automatically deprovisioned when you remove an AD user account.
Replacing the SharePoint Newsfeed with Yammer
SharePoint Online as with all versions of SharePoint 2010 and 2013 provides the Newsfeed functionality which is designed to be your timeline of information for your companies collaboration world. The Newsfeed in SharePoint is part of a users’ My Site area however Yammer being an enterprise social network provides a better capability for newsfeed and maintaining two systems for one function is redundant. Luckily, there is an option we can change that will replace the native SharePoint Newsfeed with the Yammer service.
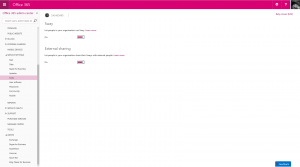
As a Global Admin, login to the Office 365 Admin Center and browse to your SharePoint Admin Center. From the SharePoint Admin Center, among the options, you will find a setting titled Enterprise Social Collaboration. Under this heading, change the setting from Use SharePoint Newsfeed (Default) to Use Yammer.com Service. As per the description for this setting, it can take up to 30 minutes for the setting to propagate all of the Office 365 servers so for a short period of time, some users may still be directed to their Newsfeed after this is changed.
Embedding Yammer Feeds into SharePoint
SharePoint is where your company stores its documents and data so it makes sense to have related comments and social interaction from staff in the same place. On the Yammer site, you can find out how to use Yammer Embed to incorporate Yammer Feeds and Pages into your SharePoint sites or even any HTML web site your company may have. You can find out more about Yammer Embed at https://developer.yammer.com/v1.0/docs/embed.
It’s worth noting here that there is currently, a Yammer Web App for SharePoint however this is being discontinued later this year therefore there is no point building a system using the Web App now as you will have to re-create it before not too long and it makes better sense to develop using the long-term solution now.
I hope this post sheds a bit more light on what Yammer is, how to get it and how to start using it.