Configuring Global Service Monitor for SCOM
As System Center people, we all know that SCOM is very powerful and capable at monitoring but unless you deploy Management Servers or Gateway Servers into a public cloud environment like Azure, all of your monitoring comes with the perspective of inside your environment. If you are hosting web services that are externally accessible, one important aspect to consider is outside-in monitoring, otherwise known as monitoring your externally facing services from outside of your organisation.
Licensing and Registering
Global Service Monitor (GSM) for SCOM has been around for quite some time now since 2013 and I still see people running SCOM who are entitled to GSM not using it. To be eligible for GSM, you most importantly need to be running System Center Operations Manager 2012 SP1 or higher. You need to have a properly licensed SCOM deployment and you need to have Software Assurance for your System Center licenses as GSM is an SA benefit if you want to use the service permanently or you can also sign up for a free 90 day trial of GSM if you don’t have SA on your licenses to try the service out as I did.
To activate your SA benefit for GSM or to register for a 90 day trial, you first need to visit the Microsoft Commerce Portal at http://go.microsoft.com/fwlink/?LinkId=275502. You need an Organisational Account to sign in here which means in a sly way, you need to be using Office 365, Azure or Intune as well or at least have a working Azure Active Directory deployment ready for you to consume one of these services in the future.
Preparing the Management Servers
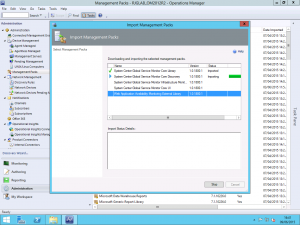
Once you get yourself either signed up or activated according to whether you are going trial or permanent, we need to download the GSM Management Pack. You can obtain this from the Microsoft Download Center at http://www.microsoft.com/en-us/download/details.aspx?id=36422. The download is a .msi file which you need to install to extract the Management Pack Bundle files.
With the files extracted but before we can install the Management Packs, you need to check you have the relevant Windows Features installed. GSM requires the Windows Identity Foundation 3.5 feature to be enabled on the Management Servers which will participate in the monitoring so make sure you install this on all the relevant Management Servers and not just the once you perform the installation on.
To avoid posting a screenshot of clicking through Server Manager and Add Roles and Features Wizards, the PowerShell Cmdlets for installing this feature is below.
Import-Module ServerManager Install-WindowsFeature Windows-Identity-Foundation
Once that is out of the way, you can import the Management Packs into SCOM.
Configuring Global Service Monitor Settings
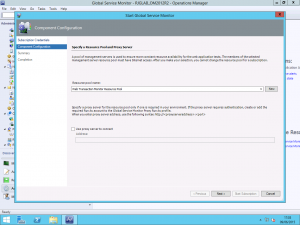
Once you have the Management Packs imported, a new view will be added to the Administration pane of the Operations Manager console for Global Service Monitor and you can start the configuration wizard. You will be asked to sign-in using your Organisational Account as part of the process and from this, your GSM Subscription ID will be discovered.
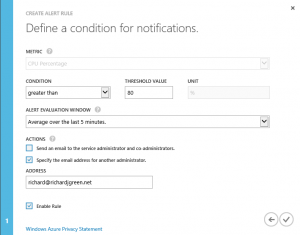
GSM uses Resource Pools for determining which Management Servers will communicate with the service. You can use the All Management Servers Resource Pool however this is not recommended. I have created a new resource pool for as recommended. You also here have the option to configure a proxy server to use to access the GSM service.
Creating Web Application Availability Monitors
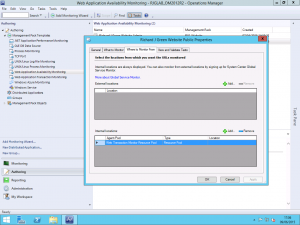
Once you have completed the wizard above and GSM is configured, you can start to configure monitors using the service. I already had an existing Web Application Availability Monitor configured for my blog so I have modified this to use GSM. It is important to note that GSM only works with Web Application Availability Monitors and not with Web Application Transaction Monitors so you will need to make sure that you are using the appropriate type. There is a good article on System Center Central that compares the two types of monitor and what each can do at http://www.systemcentercentral.com/which-is-the-best-synthetic-web-transaction-to-use-in-operations-manager-for-my-requirements-scom-sysctr/ if you need to understand the difference.
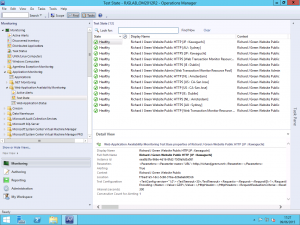
As you can see above, I have my existing Web Application Availability Monitor and I have one internal location configured, my resource pool however we have an empty field above called External Locations. Select the Add button to add a new external location.
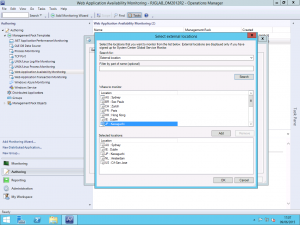
Selecting this option now presents us with a list of the available GSM monitoring locations. Those familiar with the Azure datacentre locations will note that they are the same as the GSM locations. I selected a few choice locations but which ones you use or how many is entirely up to you. If your service that you are trying to outside-in monitor is truly global, you may want to use them all but if you are only interested in the availability of your service within a particular geographic region then just use those relevant to you.
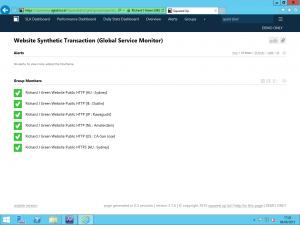
Once you apply the changes it takes a little while for the request to be sent up to Global Service Monitor and for the monitoring data to start coming back down but after a short wait, about fifteen minutes in my case, I started to see the health state for the various monitoring sites in the Monitoring view.
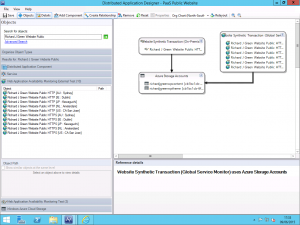
In my lab, I am using SquaredUp to provide rich HTML5 visualizations of my SCOM environment so I decided to take this a step further and I am using the Azure SQL Database Management Pack to monitor my Azure SQL databases that host my WordPress database and I built a Distributed Application for it and presented it via SquaredUp as shown below.
And there we have it, a setup and working outside-in monitoring solution for web services using SCOM and taking advantage of SA licensing benefits. One of the best things about this is that each monitored location retrieves the counters you specify whilst configuring your Web Application Availability Monitor so you get the response time, DNS resolution time and other counters for each region so you can see really clearly how latency plays a part in your applications performance.
I hope you found this useful and it helps you to monitor your own solutions with GSM.