Deployment Scenarios for Office 365 and AAD Identity
In my previous post from yesterday on understanding Office 365 and AAD federated identity types, I talked about the two methods for allowing our users to sign in to the Microsoft cloud services with our on-premises identity using either DirSync, AADSync or FIM for same sign-on or using ADFS for single sign-on. Now that we understand the products at a high-level, I want to cover off some options for deployment scenarios and specifically, how we can leverage Microsoft Azure to host these services.
Customers are increasingly trying to cut the cord with their on-premise datacenters due to the high cost of running them and are looking for cheaper alternatives to run their services. Moving our email, collaboration and communication productivity tools to Office 365 is one way that we can work towards achieving that however in consuming these Office 365 services, we remove the need for having our on-premises Exchange, SharePoint and Lync servers but we replace them with servers that are used to synchronise our identities to the cloud or provide the authentication tokens. If these servers go down it could actually have a more detremental effect than the loss of an on-premise Lync server so we need to pay close attention.
On-Premise Deployments
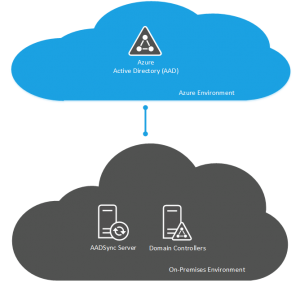
DirSync, AADSync and FIM for Same Sign-On
If you have opted for a same sign-on deployment then unless you have a specific need for FIM because you have a complex infrastructure or if you have already deployed FIM and want to leverage that existing investment you will be deploying DirSync or AADSync. DirSync is the incumbant tool and AADSync is its replacement although DirSync is still supported and will continue to be supported for a currently undefined period of time so if you have already deployed DirSync then you don’t need to rush out and upgrade your servers to AADSync.
None of these products, DirSync, AADSync or FIM support clustering or high availability which means you can deploy only one of them at a time. FIM can be sweet talked into working as a clustered product but the process is unsupported and documented by Damian Flynn at http://www.damianflynn.com/2012/10/11/fim-sync-server-2010r2-cluster-build/. If you want to provide high availability for these applications then you will need to look outside the operating system and look to your hypervisor, assuming you are deploying them as virtual machines.
For DirSync and AADSync, the easiest thing to do will be to have a disaster recovery plan and a build document for the installation so that if you’re server melts, you can deploy a new one from a VM template in short order. If you were extra paranoid, you could have a VM deployed with the DirSync or AADSync binaries on the server ready to install (but not installed) so that if you had a failure you could simply run through the installer following your build document and be up and running in about 15 to 30 minutes.
For FIM, you definately want a backup of this server because a) its not highly available and b) there are complex configurations going on here and tryring to re-create this from scratch as we would likely do with DirSync and AADSync wouldn’t be fun nor quick.
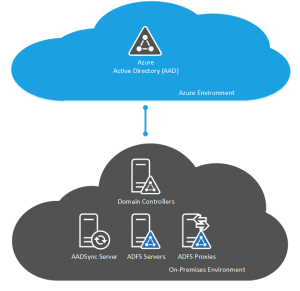
ADFS for Single Sign-On
As we know from my previous article, deploying ADFS is more involved and requires more moving parts howeer luckily, all of these parts can be clustered or load balanced accordingly. The exception to this is the DirSync or AADSync server that you deploy in addition to the ADFS servers to sync the users identities but not the password attribute to go with it.
ADFS Proxies which reside in your DMZ network segment are essentially web servers which can be load balanced. We only require Port 443 for HTTPS SSL pages to be made publicly accessible and we can use either Windows native NLB or we can use a hardware or software load balancer such as a Citrix Netscaler, KEMP Loadmaster or an A10 Thunder load balancer. As a side note of interest, Citrix and A10 both support integration into VMM so if you are using a Microsoft private cloud with Hyper-V and VMM in your on-premise network then these products can be easily integrated into your deployment approach for new servers.
ADFS servers live in your clean, corporate network and route requests between the proxies in your DMZ to the Active Directory domain controllers to retrieve the authorization for users. The ADFS servers use a Windows Internal Database (WID) as standard which supports farms of up to five ADFS servers however if you need more than five servers, you will need a seperate SQL Server for the database which we can of course cluster.
Azure Deployment
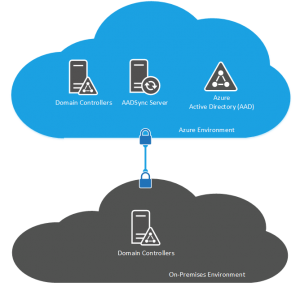
DirSync, AADSync and FIM for Same Sign-On
As I mentioned earlier, companies are interested in cord cutting the on-premise datacenter as we know so moving things into the cloud where it is possible and makes sense helps us to achieve this and more importantly, reduce the dependancy on our internal facilities. With DirSync, AADSync and FIM deployments for same sign-on, we can really easily achieve this with Microsoft Azure.
The components that make this design work are the Azure VPN which provides site-to-site connectivity between your on-premises environment and Microsoft Azure. Once you have the Azure VPN configured and working and you have your virtual network segments configured in Microsoft Azure, we need to deploy an Active Directory Domain Controller into Azure using an IaaS VM. This will hold a replica of your Active Directory database from on-premise. We then deploy the DirSync, AADSync or FIM server on an IaaS VM in Azure.
By deploying the synchronisation VM in Azure along with the domain controller, the two servers are within the same AD Site which you will have created for Azure and will allow the synchronisation server to contact AD for the user data it needs and will allow it very fast access to the Azure Active Directory service to sync your objects to the cloud directory.
For high availability in this design, we can deploy multiple Domain Controllers into the Azure AD Site and we can use the Azure VPN service in a point-to-multi-point configuration so that two of your on-premise datacenters have an endpoint for the Azure VPN so that we aren’t dependant on a single site for on-premise connectivity. Remember that with this same sign-on deployment, we can only have a single synchronisation server so it is not possible to make this element highly available. When we deploy multiple Active Directory Domain Controllers into Azure, we need to make sure that these VMs go into an Availability Set together which causes the Azure fabric to place these VMs on seperate hosts and racks in the environment so that they are not effected by maintenance operations.
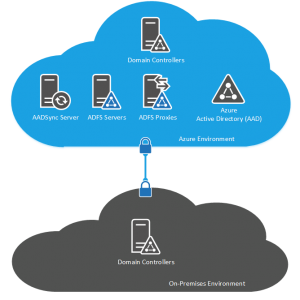
ADFS for Single Sign-On
Using Azure to deploy our ADFS for single sign-on deployment really is the way to show case the power and ease at wihch we can deploy a complex solution with Microsoft Azure. The building block of this design is the same as that of the DirSync and AADSync in that we start out with configuring Azure VPN in a point-to-point or point-to-multi-point connection to our on-premise environment and we then deploy multiple Active Directory Domain Controllers which provide our authentication source.
In deploying SSO with ADFS, we need to configure, deploy and test the ADFS environment before we deploy and configure the DirSync or AADSync server. I must atest to not fully understanding the reason for this but Microsoft recommend it so we do it. As you would do for an on-premise deployment, we deploy two ADFS Proxies which recieve our incoming token requests and we deploy two ADFS Servers which do the back and forth between our ADFS Proxies and the AD Domain Controllers to authorize users.
As we did with our previous same sign-on design for a Microsoft Azure deployment, we need to make sure we place our IaaS VMs into Availability Sets however this time we have three sets: one for our Domain Controllers, one for the ADFS Proxies and one for the ADFS Servers.
With an on-premise deployment, we need to buy and configure a load-balancer to use with the multiple ADFS Proxy servers however in Azure we can simply use the Azure Load Balancer to quickly and easily achieve this.
With the ADFS for single sign-on deployment in Microsoft Azure, if having two VMs running for each service isn’t quite enough availability for you because you are concerned about the resiliency that Microsoft provide within a single Azure datacenter, you could take the deployment to another level and use two datacenters. Using two Microsoft Azure datacenters, we split the services provided by the deployment throughout the Azure environment and use the Azure Traffic Manager to provide Geolocation awareness for users and direct them to the most appropriate ADFS Proxy for authentication. If you are deploying ADFS for single sign-on in an organisation which has users throughout the globe then this could be an ideal deployment to achieve not only your high availability requirements for IT but also to improve the user experience by sending the user to the ADFS Proxy closest to them.
Cost Consideration
All of this talk of Azure deployments is very nice but we need to be aware of our costs. Deploying services on-premises has costs associated and these costs are often a lot higher than people realise because they don’t fully take into account every facet of the infrastructure. When you are costing up an on-premise VM you will likely include the cost of the SAN disk occupation or the percentage of a host it occupies and the host of that virtualization host but are you factoring in the amount of extra power that server will consume as a result of the extra CPU cycles or the fraction of load that adds to your UPS or your network switches?
Implementing a simple deployment of DirSync or AADSync will be very cheap and I would challenge any enterprise to be able to do it themselves cheaper. A single datacenter deployment of ADFS for single sign-on will cost more to implement than same sign-on due to the increased number of servers and the addition of the Azure Load Balancer however that cost will double if you extend that to a dual Azure datacenter deployment not to mention the increased configuration complexity.
To conclude, make sure you consider the cost and complexity of what you are proposing to implement and make sure that what you plan to do is really what you need to do. If all your users are based in the UK then having that all sining, dual datacenter, multi-point Azure VPN deployment split across the UK and East Coast US with Geolocation Traffic Management probably isn’t what you really need and you will be wasting resources in both money to pay for it and time and complexity to manage it.