Azure Web App SSL Cipher Suite Changes
Earlier this week, I got an email form the Azure Team to announce that as part of security improvements to the Azure App Service Web Apps (formerly known as Azure Websites) they will be making changes to the supported SSL cipher suites with the changes taking effect as of July 18th 2015. Additionally, Microsoft have provided a test site that is running the new suite of ciphers at https://testsslclient.trafficmanager.net.
I decided to take the test site for a drive over on the Qualys SSL Labs tool the SSL Server Tester. I’ve been using this site for a long time now as a means to test SSL enabled websites as it allows you to verify the whole configuration in one place including the certificate, protocols and cipher suites. I ran the test site through Qualys SSL Server Tester as well as this blog which is running on a current generation Azure Web App site to compare the results.
It’s important to understand the difference between a Web App and a Cloud Service before we get much further into this too. Some people will be looking at this post and thinking why don’t I just enable or disable the relevant protocols or ciphers within my application however herein lies the difference between the Web App and a Cloud Service. The Web App in web hosting terms is a website running on a multi-instance web server. A Cloud Service is a dedicated instance that you are responsible for so allow you more control but at the expense of additional complexity. With a Cloud Service, we can configure the ciphers and protocols as part of the service definition which runs in the form of a start-up script. With a Web App, we don’t have any of these levels of deep system level access so have to accept what we are given.
Running the test on this site, richardjgreen.net I get the same result I have achieved for some time, a overall score of Grade B. The grade in this instance is limited to B because the server is allowing weak RC4 ciphers as well as a Triple DES (3DES) cipher. Additionally, the current site does not support Forward Secrecy, sometimes seen at Perfect Forward Secrecy or PFS for short. The final message stating that the site only works with browsers supporting Server Name Indication or SNI for short is not a security failure. This is due to the fact that I have opted to only support SSL for SNI browsers on my Azure Web App instance.
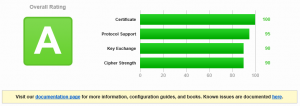
Running the test again against the test site, we can see that the result has improved to an overall score of Grade A. This is achieved because support for the weak RC4 ciphers has been dropped along with the Tripe DES (3DES) cipher. Additionally, the cipher suites have been re-ordered slightly and a new SHA384 3072 RSA key cipher has been added at the top of the cipher suite order meaning that this cipher should be the most preferable to use.
Looking at some of the details for the test, I also appears that the Web App instances are being built now on Windows Server 2012 R2 although how long this has may have been the case, I do not know? In the HTTP Server Signature for the SSL Server Tester results, richardjgreen.net shows Microsoft-IIS/8.0 whereas the Microsoft test site shows Microsoft-IIS/8.5.
I look forward to re-running the SSL Server Tester after the 18th July and seeing if the test result for my own site is as good as the test site shown.