Microsoft Enhanced Mitigation Experience Toolkit (EMET) is something which has seemingly been around for years, a little known and less travelled piece of Microsoft software. In this post, I’m going to explore what EMET is, what it has to offer and briefly how it works.
What is Microsoft EMET
Microsoft EMET (Enhanced Mitigation Experience Toolkit) is a piece of software which can be deployed to assist in a defence-in-depth strategy to protect computers running Microsoft Windows. EMET employs deep hooks into applications monitoring them as they run looking for suspicious activities. Because EMET monitors code activity for patterns common to attacks, it is heuristic in it’s nature which means there are no definitions to keep up to date like anti-virus software which work by protecting against known attacks. EMET isn’t looking for the known but instead, for the unknown.
Believe it or not, EMET has been around for sometime although it’s largely never heard of. Even me as a Microsoft bigot hadn’t heard of EMET until about six months ago when I accidently stumbled upon it.
EMET has been available since 2009 in the dawn of Windows XP with new versions slipping out on a regular basis. The current general availability release is version 4.1 Update 1 and there is a version 5.0 available in Technical Preview. The current version 4.1 Update 1 supports operating systems from Windows XP Service Pack 3 all the way up to Windows 8.1 and Windows Server 2012 R2. Version 5.0 Technical Preview only supports Windows Vista Service Pack 2. Whether this is down to the end-of-support for Windows XP and therefore a purely commercial withdrawal from Windows XP is unknown but in that EMET is a 32-bit process even on 64-bit installations of Windows, it would be nice to think that there is some evolution happening and not just iteration.
Who is Microsoft EMET Designed For
EMET is not designed for home use due to the potentially complex nature of it’s configuration. You could safely deploy EMET at home if you left it in it’s default state protecting Office, Adobe Reader and Java but I probably wouldn’t recommend it without knowing what you are doing. EMET is designed for enterprises who want to add an additional layer of defence and protection to their client computers in addition to anti-virus and firewall software.
What Does Microsoft EMET Protect
Out of the box, EMET will protect Internet Explorer, Microsoft Office, Adobe Reader and Oracle Java but due to the way in which EMET is built, it can be extended to protect any application you desire but this needs to be taken with caution. Enabling certain mitigation hooks can cause applications to crash if EMET believes a certain operation is malicious when in fact it is desired behaviour. Microsoft have a list of known issues with EMET and application compatibility at http://support.microsoft.com/kb/2909257. There are various threads on the TechNet Forum discussing other compatibility issues with EMET.
The key takeaway is that you need to test EMET thoroughly before widespread deployment. Enabling mitigations in EMET can easily break an application or a whole system if you enable mitigation for an application which is key to hardware or operating system function (such as the known issue with ATI Video Drivers for example).
Reading the Microsoft Security Research and Defence Blog at http://blogs.technet.com/b/srd/ you can read some pretty complex and deep dive information on how that various mitigations in EMET work, how EMET has been able to thwart some of the more recent exploits from day zero. I for one don’t at this moment in time understand the what SEHOP means or how that protects me, I just know that it does although I do intend to read up on these various protection types.
What Does Microsoft EMET Cost
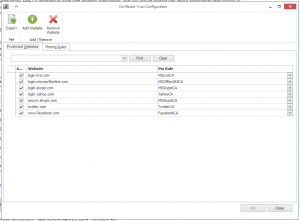
Nothing, it’s free for anyone who wants to download and install it. It’s worth noting that currently, only EMET version 3.0 is available for support through the Microsoft support channel of Microsoft Premier Support for enterprises. This is a very good reason to make sure you test the deployment of new mitigations in EMET before deploying them but I would consider whether deploying EMET 3.0 is the right thing to do regardless of support. EMET 3.0 is quite an old version and misses out on the newest certificate trust pinning feature.
Microsoft EMET Client Deployment
Microsoft EMET is installed using a traditional .msi file which can be manually installed or can be deployed with Group Policy Software Installation, System Center Configuration Manager or a third-party application management solution.
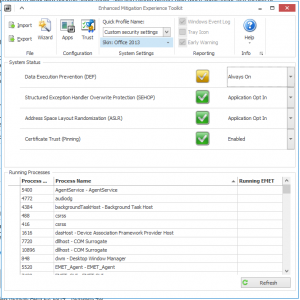
The client when launches shows the current status for the four main protection types, DEP, SEHOP, ASLR and Pinning. DEP is a protection type which should be quite common for most system administrators as a Windows feature since Windows XP however SEHOP and ASLR will likely require some research. Pinning is a new feature in EMET 4.1 which allows you to protect against certificate man in the middle attacks. EMET locks the signature of trusted certificates such as those for Microsoft Windows Live, Office 365, Skype, Facebook and Twitter. This is a really nice feature and one that I’m personally a fan of although I would like to see more certificates listed by default such as Google.
If you opt for the EMET 5.0 Technical Preview, there are additional new features also but being a Technical Preview, you are even further beyond the scope of support so do this at your own risk for sure.
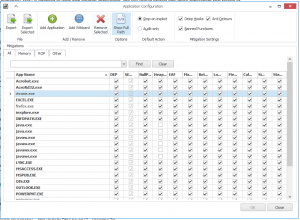
The Apps configuration list allows you to enable and disable mitigations for specific applications as well as define custom applications to be protected by EMET.
Microsoft EMET Client Configuration
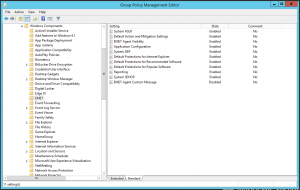
When configuring EMET you have a number of options. You can either do this per client manually, using Group Policy with the provided ADMX file or with a configuration export. A configuration export gives you the most flexibility however it requires you to have a reference computer configured with EMET to your current specification. Once configured, you can export the configuration to a file which you can then import to other EMET clients automatically using System Center Configuration Manager for example.
Configuration using Group Policy is simple and allows you to control almost everything such as the status for system-wide protections and to configure user-defined application protections including which mitigations to apply for them however it does not appear to allow you to configure the certificate trust pinning. I’ve used Group Policy in my scenario as it was the easiest for me to implement and administer.
Is Microsoft EMET Worth Deploying
This is a good question and one I considered before I deployed it at home for myself and I came to the conclusion of yes. Windows 8.1 is a good operating system with lots of protections included out of the box such as Windows Defender and Windows Firewall. It is regularly updated and patched to address performance, security and other issues by Microsoft closing holes as they are found and the success of the Windows Update service means that this patching is commonplace and reliable. System Center Endpoint Protection 2012 R2 which I use as my anti-virus protect does a great job of scanning for known viruses but as was said in a recent interview with a top dog from Symantec, anti-virus is “dead” (http://www.engadget.com/2014/05/06/symantec-declares-antivirus-dead/). Protecting systems at as many other levels as is viable and logical to do so therefore makes a lot of sense and a product which is free from Microsoft can only help to do this.
On my PC at home I have EMET running in the recommended security configuration and the process is consuming 14.9MB of memory. On my fairly standard desktop PC with 8GB or my Surface Pro tablet with 4GB RAM, 14.9MB is nothing to even think twice about and for that little bit of memory consumption, it’s a little extra piece of mind keeping me safe at all times.
If you try out EMET for yourself or if you have used it previously, please get in touch and let me know what your personal experiences are. I’d like to hear from anyone with previous experience with EMET due to the somewhat unknown nature of this product.



